Finding secrets in source code
Unearthing Secrets From Code Repository
As part of my day job, i have been tasked with finding critical secrets within high value GitHub project. Obviously, i am not talking about a public project, but internal repository within the company. Since the multi-million-dollar company i work for didn’t have a single cent to throw at the problem, i found myself looking towards the open-source project.
Trufflehog
There is 2 tiers associated with Trufflehog, the paid one, and the OSS one. Strictly from the OSS point of view, the tool allows you to dig into GitHub repository and find leaked credentials. This tool can be leveraged either as a proactive measure or in an offensive security fashion. You can run it locally, on your machine, or inside a runner to scan the entire company. I won’t go into much detail on the orchestrated option, but we will dig a bit into the local options.
The open-source tier is packed with detectors. At the moment of writing, there were about 639 different types of detectors available : https://github.com/trufflesecurity/trufflehog/tree/main/pkg/detectors
Download and first execution
Head over to Trufflehog GitHub repository and download the latest release related to your operating system :
https://github.com/trufflesecurity/trufflehog
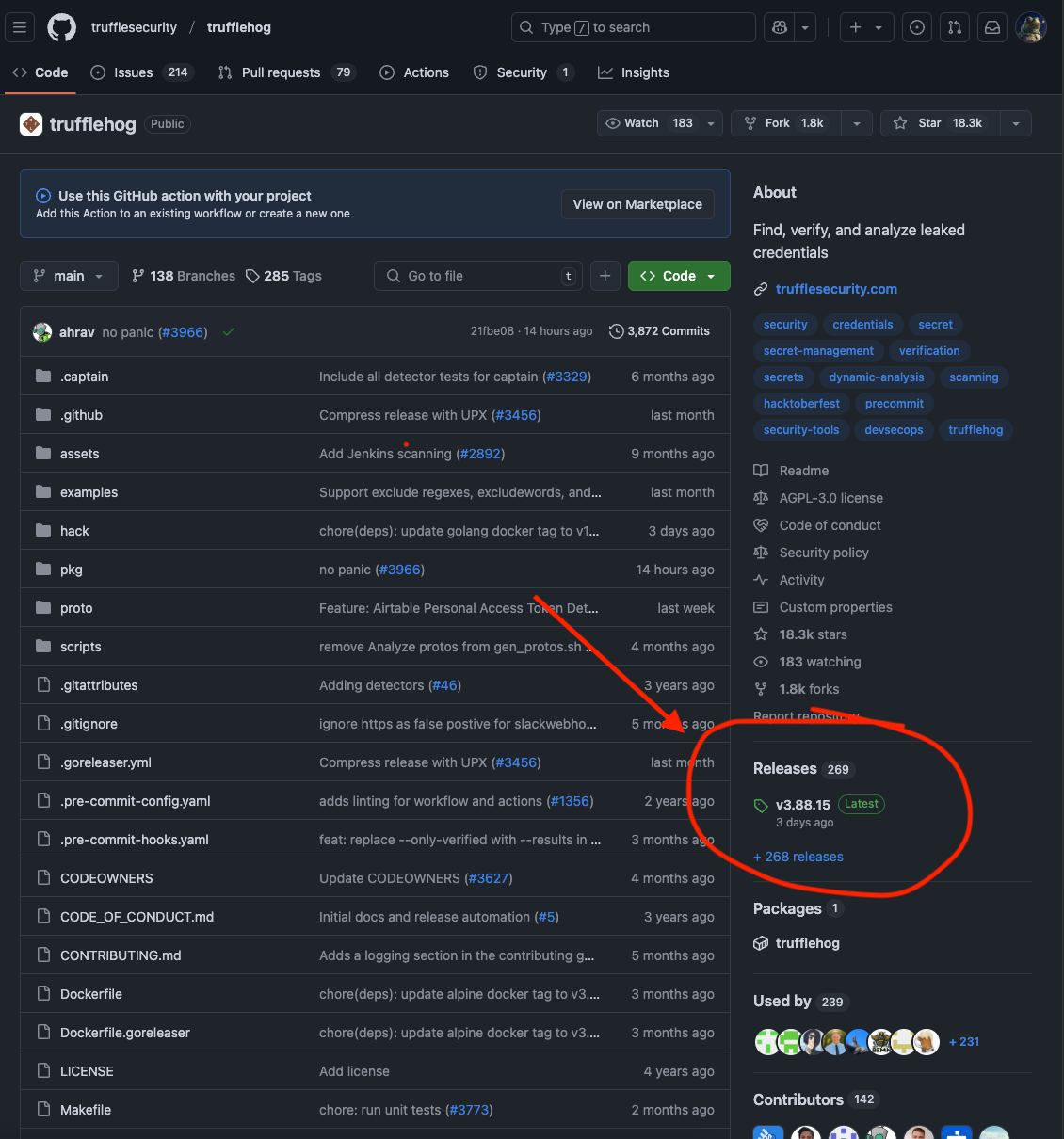
You can run Trufflehog either as a single script, or build it from the source. You’ll need Go installed.. That’s for another post.
Once downloaded and extracted / untar-ed, verify that Trufflehog is working properly:
./trufflehog --version
If you have an output like below, you are good to go (the version is dependent on the binary/ release version you downloaded).
trufflehog 3.88.15
Scanning repository for secrets
Now, how can you scan a repository for secrets ? Pretty simple. There are some parameters you can pass to Trufflehog, we will go into more details below. For demonstration purpose, i will be using the public repository called “OSSF Scorecard”, an open-source project for assigning trust value to OSS dependencies : https://github.com/ossf/scorecard.git
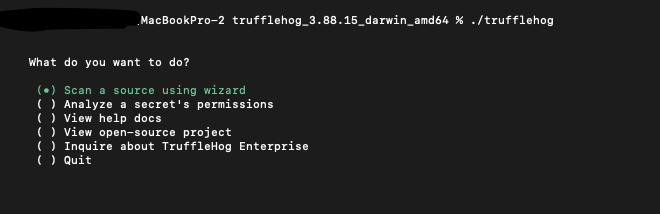
If it’s more your type, you can also run Trufflehog within the terminal text UI :
./trufflehog
You can also pass some parameters directly to the ./trufflehog script. The command below will check all the git history and current one, for leaked secrets - valid or invalidated. The output can be quite verbose in big repository with a lot of activity, but this should be the first step in evaluating a repo for leaked credentials :
./trufflehog git https://github.com/ossf/scorecard.git
As you can see, the output below returned more than 5000 unverified result :
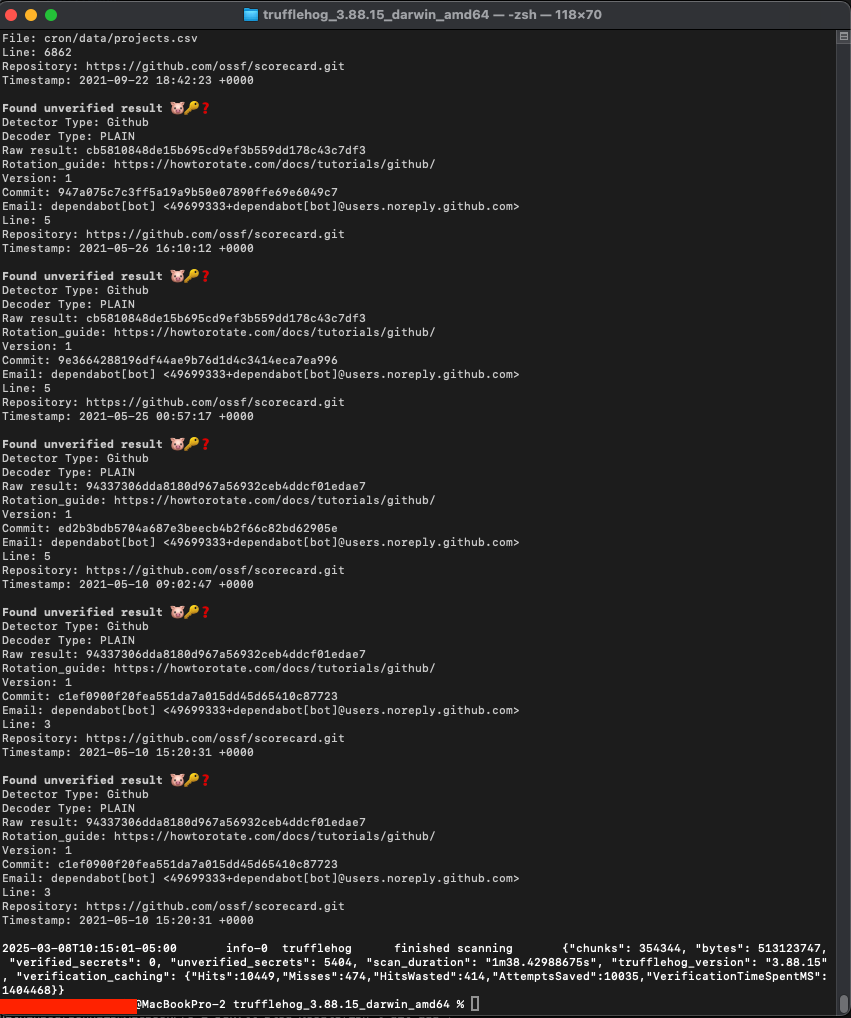
Now we can start digging down to check only for verified result (Note that Trufflehog will try its best to evaluate the entropy of a secret and try to make some API calls to determine if a secret is possibly valid) :
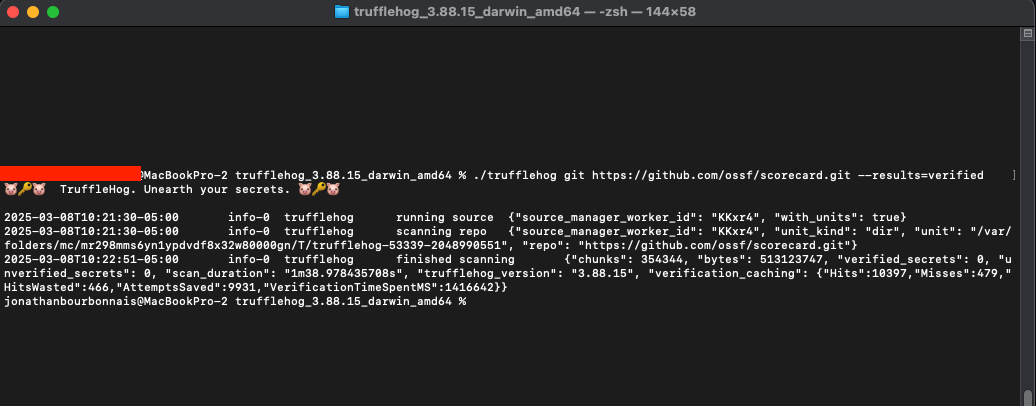
./trufflehog git https://github.com/ossf/scorecard.git --results=verified
The good news in the example is that Trufflehog did not find a single verified leaked secrets. Note that this is not a POC of exploitability, you don’t have to look for long in public repo before you find valid credentials ;)
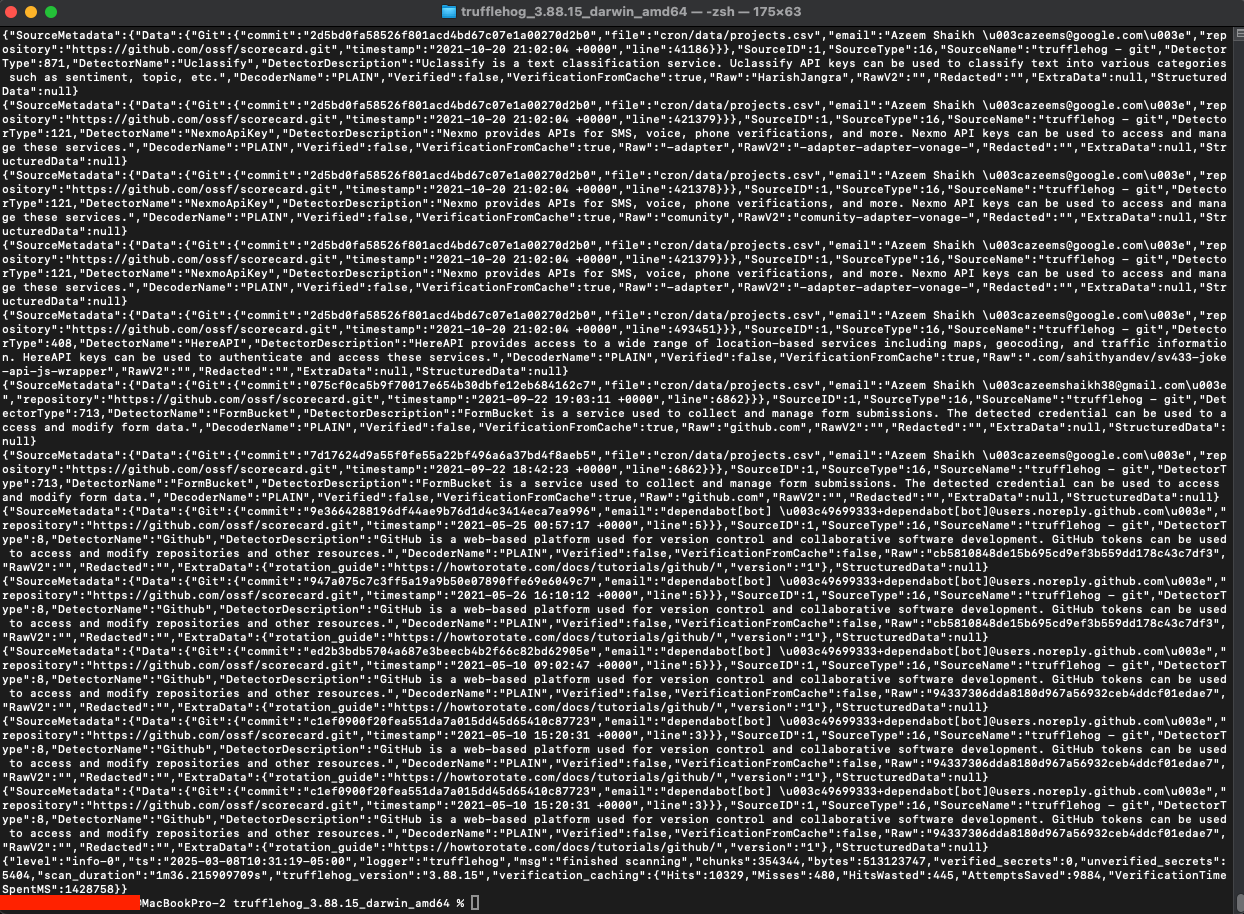
If you have a lot of output, you can pass the json parameter to output in a much more workable format and tune up the number of concurrent jobs (default is 8) :
./trufflehog git https://github.com/ossf/scorecard.git --json --concurrency=10
Running Trufflehog inside a container
You can run Trufflehog inside a container for various reasons. For automation challenge, this is the way to go (just rename the git repository for the selected target) :
docker run --rm -it -v "/tmp:/tmp" -v "$PWD:/pwd" trufflesecurity/trufflehog git https://github.com/trufflesecurity/test_keys.git
How to test found credentials ?
This is depending on the type of secrets you did find. The process will not be the same if you find SSH key vs. API key. The easiest to test is probably, in my opinion, the API key. With a simple curl command, you can validate the credentials you found. Here is a pretty good blog post about API calls if you don’t know anything about that : Baeldung.com - curl
Wrap-up
In short, Trufflehog can be leveraged as part of an audit, a cyber defence strategy or even for an offensive security campaign. Leaked secrets are a real problem in modern SDLC and the more you dig, the more you realize it is. Leaked API credentials, especially in public repository can have a huge impact on the organization. With a tool like truffle that is scanning your entire git history, a mistake that was made 10 years ago can come back and haunt you down the line. In the next part of this series on Trufflehog, we will dig deeper into the capabilities of the tool and hunt for real secrets in public projects.